 Gold Application Development
Gold Application Development
Gold Data Analytics
Gold Cloud Platform
Gold Cloud Productivity
Gold Enterprise Mobility Management
Silver Messaging
Silver Collaboration and Content
Silver Small and Midmarket Cloud Solutions
Certified Gold Partner for over 20 years

Identity & Security
The Challenges
- I need to be able to modernize Identity, Authentication and Access Management, allowing for the latest functionalities, such as Multi Factor Authentication and Single Sign on
- How do I ensure my users have access to the applications and rights they need to work?
- I want to receive the benefits of moving to a Cloud Provider, but I don’t want to re-architect identity and access management
- I don’t want to rely on VPN for Authentication
- “Identity is the new Edge” Hackers are consistently finding new creative ways to breach credentials in your organization, and impersonate your executives
You’ll need to determine:
- Which apps require additional security
- What threat vectors pose the largest threat
- Which apps you can “lift and shift” directly to the cloud.
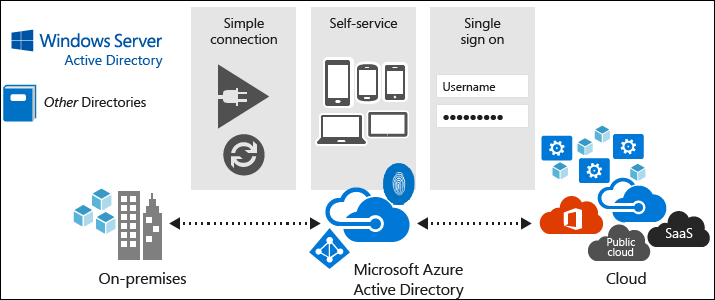
Path to the cloud for existing Identity, Access, and Security Management
There isn’t a single, one-size-fits-all strategy for Identity in the cloud. The right migration strategy for you will depend on your organization’s needs and priorities, and the kind of applications you are migrating.
Each migration approach has different benefits and reasons for using it. You can choose a single approach when you migrate apps to the cloud or choose certain components from multiple approaches. Individual applications aren’t limited to a single approach or maturity state. For instance, a common hybrid approach would have certain on-premises components plus other components in the cloud.
Each migration approach has different benefits and reasons for using it. You can choose a single approach when you migrate apps to the cloud or choose certain components from multiple approaches. Individual applications aren’t limited to a single approach or maturity state. For instance, a common hybrid approach would have certain on-premises components plus other components in the cloud.
At the first two migration levels, you can just lift and shift your identities:
Level 1: Cloud Identity-Ready: In this scenario you are likely using Active Directory but may not have any Cloud Identity Infrastructure. We can help you plan your identity and security and ready your current Identity infrastructure that allows you to replicate your identities into Azure Active Directory and allows users to leverage this Identity Platform to sign into their applications using existing credentials. Deployments can include Federation infrastructure, or a fully cloud synced identity
Level 2: Cloud Identity-Hybrid: At this level, after an initial lift and shift, and still without re-architecting or altering your current Active Directory Infrastructure, we can assist you in securing identities and ensuring only authorized users on authorized devices can access your applications and intellectual property. Deployments can include Seamless sign on and Multi Factor Authentication. This deployment can include seamless experience in locking down applications, devices, documents, and other intellectual property information repositories; including automatic risk mitigation and the classification of intellectual property, ensuring the right person, on the right device, and even down to the right file!
The third level of maturity is the ultimate goal in the cloud, but it’s optional for many apps and not the focus of this guide:
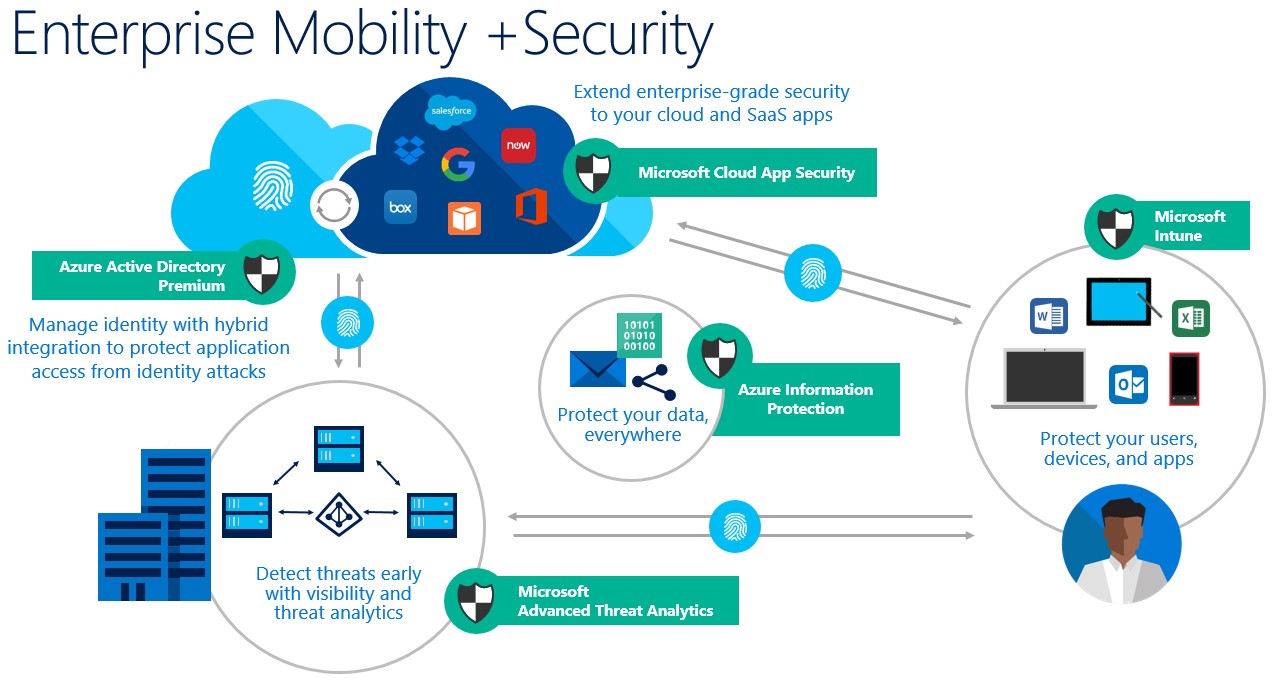
Level 3: Cloud-Identity and Security: This migration approach typically is driven by business need and targets modernizing your stance on Identity Access and Security. With your identities locked down and highly available, the fun of enabling automatic risk mitigation, bad actor threat behavior analytics, and information protection will allow the enterprise to remain secured. Automatic file classification allows to ensure the right person, on the right document, has access to only the intellectual property they are supposed to. Privileged identity management also ensures that IT Admins only escalate their rights when needed and those activities can be closely audited.
Key technologies and architectures
Microsoft Active Directory debut as a Preview in 1999, bundled with Windows Server 2000. Before this, the only authentication mechanism available was LDAP. Since then, Active Directory has been the foundation of every modern corporate network, managing Identities and authentication to resources and applications. Since then, Microsoft has consistently extended functionality of Active Directory and Identity capabilities into the Cloud with Azure Active Directory, Intune, and the Enterprise Mobility Suite.
How can B2B help?
At B2B Technologies, we can
-
- Review your current Architecture and determine what Identity options are available to you.
- Create Secured Cloud Identity plans for each of your applications.
- Implement Cloud Identity plans for each of core user applications.
- Fill any gaps in your team throughout the Cloud Identity Modernization process.
